Run a Sample Audit to see what’s really happening on your site.
ObservePoint is a full-scale automated web governance solution that audits your websites to:
Take a peek at these capabilities by running a complimentary Sample Audit on 50 of your web pages. The Audit will begin immediately and you will receive an email with the report when it’s done.
Validate analytics, MarTech, and data collection
Test experiences on landing pages and conversion paths
Monitor for potential data privacy issues
Alert you when something breaks
ObservePoint is a full-scale automated web governance solution that audits your websites to:
Take a peek at these capabilities by running a complimentary Sample Audit on 50 of your web pages. The Audit will begin immediately and you will receive an email with the report when it’s done.
Validate analytics, MarTech, and data collection
Test experiences on landing pages and conversion paths
Monitor for potential data privacy issues
Alert you when something breaks
What to expect with your Audit Report:
Pages Scanned
50
DOMAIN AUDITED: domain.com
Typically a 50 page smaple provides a good high level of indication of what’s happening on our website, it’s just a starting point. To govern at scale we recommend auditing the most impotant pages on your website at a regular cadence even as frequently as daily. A full scan of your entire index should be performed at least quarterly
View full list of all pages found in this audit
Pages Scanned
10
DOMAIN AUDITED: domain.com
Typically a 50 page smaple provides a good high level of indication of what’s happening on our website, it’s just a starting point. To govern at scale we recommend auditing the most impotant pages on your website at a regular cadence even as frequently as daily. A full scan of your entire index should be performed at least quarterly
View full list of all pages found in this audit
Pages Scanned
30
DOMAIN AUDITED: domain.com
Typically a 50 page smaple provides a good high level of indication of what’s happening on our website, it’s just a starting point. To govern at scale we recommend auditing the most impotant pages on your website at a regular cadence even as frequently as daily. A full scan of your entire index should be performed at least quarterly
View full list of all pages found in this audit
Pages Scanned
50
DOMAIN AUDITED: domain.com
Typically a 50 page smaple provides a good high level of indication of what’s happening on our website, it’s just a starting point. To govern at scale we recommend auditing the most impotant pages on your website at a regular cadence even as frequently as daily. A full scan of your entire index should be performed at least quarterly
View full list of all pages found in this audit
Use Case Overviews describe strategies for using ObservePoint to answer specific questions and accomplish important business objectives.
The three main use cases here are a practical way to frame how our solutions can provide immediate insights about your websites. We monitor your pages, tags, and cookies to help answer these questions and more.
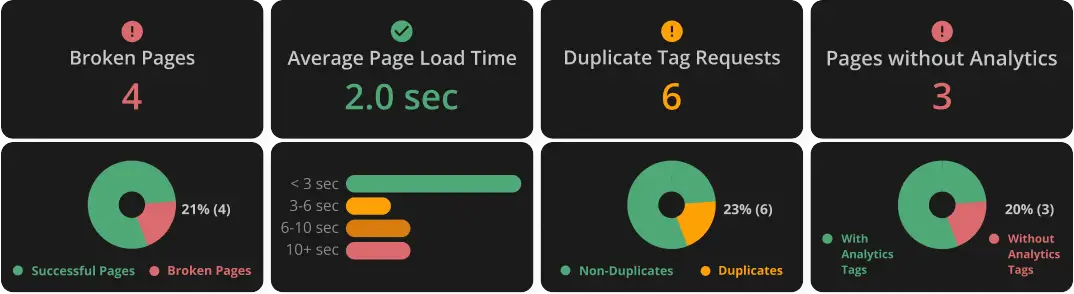
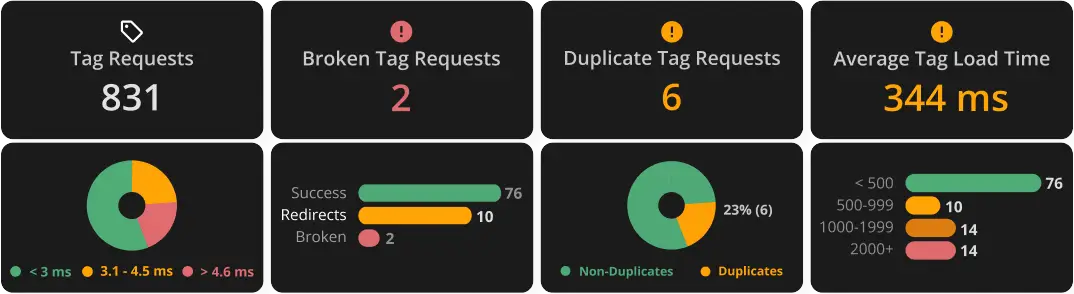
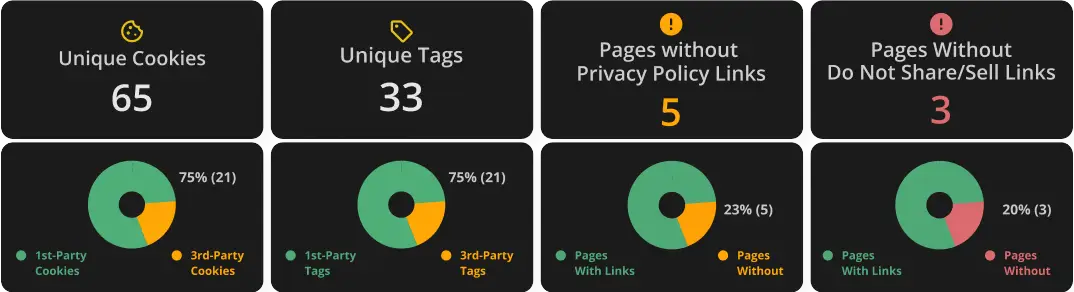
Key Findings like average page load time, duplicate tag requests, broken pages, and more will also be included.
